Quantum VPN: What it is and why it matters
A quantum VPN is a virtual private network designed to protect your internet data from the coming threat of quantum computers. Unlike traditional VPNs that rely on encryption algorithms vulnerable to quantum attacks, quantum-safe VPNs use post-quantum cryptographic algorithms.
This is vital, because quantum computers are rapidly advancing and could one day break widely used encryption methods, exposing sensitive data. What’s more, threat actors are already harvesting data to decrypt later when quantum computers become available.
ExpressVPN is among the first VPNs to adopt post-quantum encryption in both the Lightway and WireGuard protocols, offering protection designed for the quantum era. In this guide, we’ll explain the differences between traditional and quantum VPN encryption, why you need a quantum VPN, and how to choose and deploy one.
Understanding VPN security in today’s digital world
How VPNs protect your data
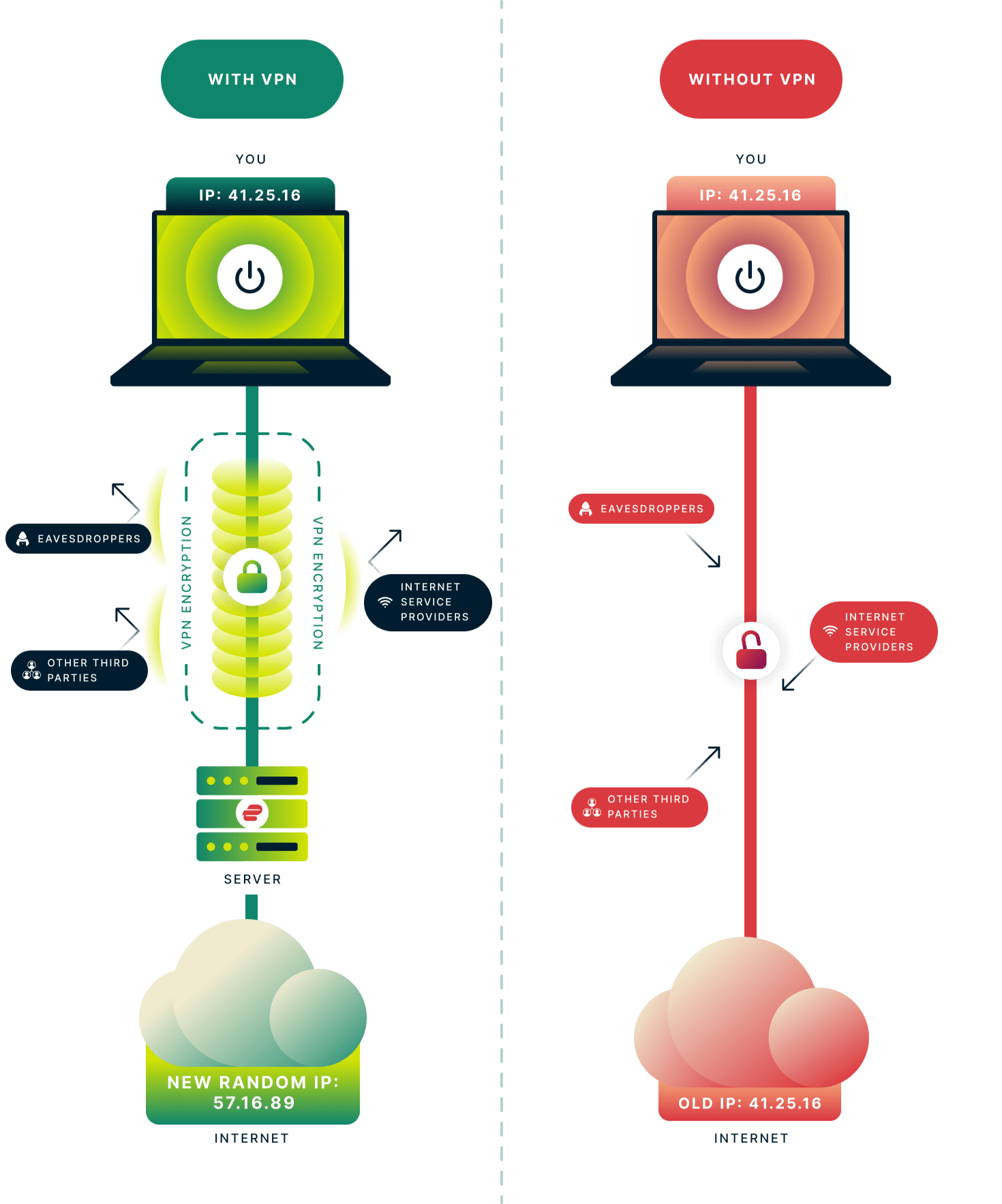 VPNs protect your data by encrypting your internet traffic and routing it through a secure server.
VPNs protect your data by encrypting your internet traffic and routing it through a secure server.
Simply put, encryption is a data protection mechanism that scrambles readable data into an unreadable ciphertext, making it useless to anyone who intercepts the data. The encrypted data will become readable again when it reaches the intended recipient, who should have the correct decryption key to unscramble the encryption.
This is why VPNs are great for staying protected on open public Wi-Fi networks: they keep public Wi-Fi admins, internet snoops, and cybercriminals guessing as to what you transmitted over the network.
VPNs use encryption algorithms such as Advanced Encryption Standard (AES) and Rivest-Shamir-Adleman (RSA) to help protect your online privacy. These algorithms rely on complex mathematical problems that current computers, no matter how powerful, can’t solve in a feasible time. For instance, AES 256-bit encryption would require a computer to try 2^256 possible key combinations to get the right decryption key, and the best supercomputer today would need hundreds of millions of years to achieve this.
The quantum threat to traditional encryption
While quantum computers already exist, large-scale quantum computers capable of breaking current encryption standards are still some years away. However, they’re definitely on the way, and that poses a huge threat to traditional encryption methods.
Unlike the most powerful supercomputers we have today, quantum computers can do more complex calculations in far less time. For example, while RSA encryption would take modern computers hundreds of millions of years to crack, once you throw the same encryption at a fully operational quantum computer, it could be broken in a matter of minutes to hours.
A quantum computer currently in development was already used to successfully break an elliptic curve cryptography (ECC) encryption key, while another breached RSA encryption.
Why quantum computing breaks current VPNs
The best VPNs rely on AES 256-bit encryption, a widely used method for securing communications and storing data that is considered virtually unbreakable by security experts. Some VPNs also use the 128-bit encryption protocol, which uses a shorter secret key than AES 256 but is still considered secure for many applications.
However, quantum computing models like Grover’s algorithm could reduce AES protection by half. This means the quantum computer would only have to go through 2^64 combinations to figure out the decryption combination for AES 128-bit encryption, rather than 2^128. The same applies to the AES 256-bit model, which would now be reduced to 2^128 combinations.
Of course, that’s still a lot of work for the computer to do. However, it shows that advancements in quantum technology may lead to further erosion of the effectiveness of these encryption algorithms.
Examples of vulnerable encryption methods
The most widely used encryption protocols we have today are all vulnerable to quantum computers.
RSA
RSA is an asymmetric encryption that relies on the difficulty of factoring very large numbers. But Shor’s algorithm, a quantum computer algorithm, excels at resolving the factors of very large prime numbers faster than current computers can manage. Some researchers have even demonstrated how to factor an RSA 2048-bit encryption with quantum computers in just 8 hours, and these computers aren’t even at full capacity yet.
ECC
ECC relies on the complexity of solving discrete logarithms. This is often regarded as more secure than RSA, since it can use a smaller key size than RSA to generate a comparable or even greater level of security. The problem is, Shor’s algorithm is also great at solving discrete logarithms, putting ECC in its crosshairs.
AES
AES uses symmetric cryptography, while RSA and ECC are asymmetric. However, AES is most likely to be targeted by Grover’s algorithm, which is better at speeding up brute force attacks. Grover’s algorithm can reduce the search area for the right combination used to secure an AES-encrypted file, then help find the answer faster.
What is a quantum VPN?
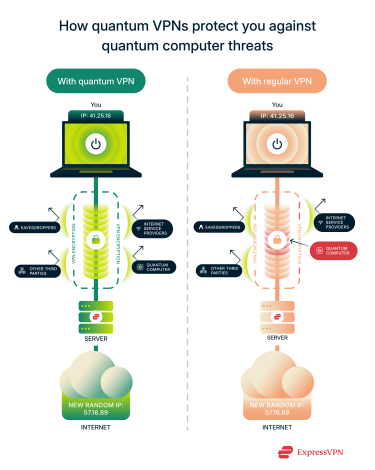 Most VPNs today rely on classical encryption techniques. With quantum computers expected to come online within a few years, regular VPN encryption may become useless against the sheer power of these computers.
Most VPNs today rely on classical encryption techniques. With quantum computers expected to come online within a few years, regular VPN encryption may become useless against the sheer power of these computers.
That’s where quantum-resistant VPNs come in: they’re equipped with post-quantum cryptography (PQC) to keep your data secure against threat actors using quantum computers in the future.
How post-quantum cryptography (PQC) works
PQC increases the complexity of the mathematical problems underlying encryption. That way, even quantum computers will struggle against these problems, which translates into continued digital data security.
But how do we find these mathematical problems? Organizations like the U.S. National Institute of Standards and Technology (NIST) have already started evaluating a number of them, including:
- Lattice-based cryptography: Rather than presenting a problem in 2D, lattice-based cryptography models like Module-Lattice-Based Key-Encapsulation Mechanism (ML-KEM) offer complex math problems in high-dimensional lattices. These problems may ultimately be solved by quantum computers, but it would take an unreasonable amount of time for them to do so.
- Code-based cryptography: This cryptographic method uses error-correcting codes for encryption. Basically, the original message is encrypted with a code in which some errors have been intentionally introduced. Therefore, the code can’t be successfully decrypted if there’s no knowledge of where the error is, what the error is, and how to fix the error before decoding is done.
- Hash-based cryptography: Hash-based cryptography is founded on hash functions, which convert information into a fixed length of jumbled data that looks nothing like the original. Hash-based functions are easy to implement, fast, don’t require massive key sizes, and are highly efficient against classical and quantum systems, making them a prime candidate for PQC.
These are just some of the cryptographic algorithms being assessed to help tackle the quantum threat.
Real-world use cases for quantum VPNs
Quantum VPNs are critical for a series of data privacy and security reasons, including:
- Securing government communications: Quantum VPNs can help governments maintain data confidentiality and integrity for sensitive state secrets, military communications, and diplomatic documents.
- Business protection and compliance: With quantum VPNs, organizations can future-proof the protection of their sensitive data. In organizations where user data is collected and processed, PQC from quantum VPNs can also help ensure regulatory compliance.
- Financial security: Banks and other financial institutions are often prime targets for cybercriminals, given the sensitivity of the data they collect, manage, and store. Adopting quantum VPNs now can help prepare them for the future.
- Internet of Things (IoT): IoT devices gather a ton of user data, which they often have to upload to a cloud server. Quantum VPNs secure IoT data collection and sharing pathways, preventing attackers from stealing sensitive personal and corporate data.
- Research and proprietary data protection: Research and development often cost a lot of resources (time and money), which is why it’s crucial to protect all related networks, systems, and data.
Again, the quantum threat is likely to be at least 5-10 years away. Even so, you should know that some attackers are already harvesting data (such as intellectual property and banking secrets) and waiting until quantum computers are ready to decrypt that data. To avoid these “harvest now, decrypt later” attacks, it’s best to start protecting your sensitive data with quantum-resistant cryptography now.
Building blocks of a quantum-safe VPN
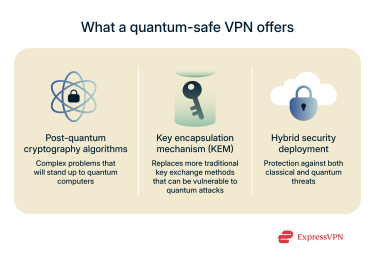
Post-quantum cryptography algorithms
Current cryptography algorithms like RSA and AES have already proven to be vulnerable to the quantum computing threat. Therefore, it’s important that quantum-safe VPNs adopt and enable algorithms that will stand up to these powerful, next-gen computers.
Generally, these PQC algorithms provide more complex mathematical problems than are currently available with AES and RSA. That ensures that quantum computers can’t decrypt the data protected by these algorithms in a reasonable amount of time.
This is why ExpressVPN integrated ML-KEM into its Lightway protocol. ML–KEM has been endorsed by NIST as a viable protection against quantum computer threats. ExpressVPN has also launched a post-quantum implementation of the WireGuard protocol and published a full technical whitepaper to give other VPN providers an instructional resource.
Key encapsulation mechanism (KEM)
To communicate securely over a public network, two parties need to establish a shared secret key that allows them to encrypt and decrypt their messages. However, sharing this key safely, especially over an untrusted connection, requires a secure method that prevents eavesdropping or tampering.
KEM solves this by letting one party generate a shared key, encrypt (or "encapsulate") it using the other party’s public key, and send it over. The recipient can then decrypt (or "decapsulate") it using their private key. This ensures that even if someone intercepts the message in transit, they can’t access the key.
Traditional methods like Diffie-Hellman (DH) are widely used and secure against classical computers. But they're vulnerable to quantum computers, which could one day break these systems using algorithms like Shor’s. This poses a serious risk to long-term confidentiality.
This has motivated organizations like Apple (with the launch of PQ3 in 2024) and Signal (with the adoption of PQXDH in 2023) to transition toward PQC, including post-quantum KEMs. For technologies like quantum-safe VPNs, adopting a post-quantum KEM is essential to ensure future-proofed secure communication.
Hybrid cryptosystems and crypto-agility
Quantum computers may be coming, but classical systems still threaten your data security, too. A hybrid approach that secures against both classical and quantum threats makes sense to ensure backward compatibility and a smooth transition period. Otherwise, older systems that can’t implement the new encryption algorithms may be left unprotected against threat actors, even while the VPN is running.
Hybrid cryptosystems offer a double layer of protection against quantum computing attacks. This hybrid approach is exemplified in ExpressVPN’s hybrid post-quantum Lightway protocol design.
Once enabled, ExpressVPN users continue to enjoy protection against modern computer attacks, thanks to the always-active AES 256-bit encryption. On top of that, users get lattice-based cryptography, a form of PQC, to secure their digital communications and internet activities against quantum computer attacks.
Why enterprises should consider quantum VPNs
Businesses and large corporations are vulnerable to data breaches and loss of intellectual property. This means that using the most advanced security technologies available to protect this data is vitally important.
On top of that, upgrading your online security suite with a VPN ready for the post-quantum world can help with regulatory compliance. By upgrading now, you can avoid being targeted by a quantum computing attack in the future, which could expose you to hefty fines and reputational damage.
Early adoption could also make your business more desirable to partners, investors, and other relevant stakeholders. They’re likely to appreciate the added safety and security that your quantum-safe deployment now grants all interactions they have with you.
Best practices for deploying quantum VPNs
Migration strategy for enterprises
It’s best to have an ongoing, flexible strategy for deploying a quantum VPN. There are currently a lot of moving pieces to consider, from what the true capabilities of quantum computers will be to the efficacy of currently researched PQC algorithms.
Follow the steps below to make the move to a quantum-ready VPN.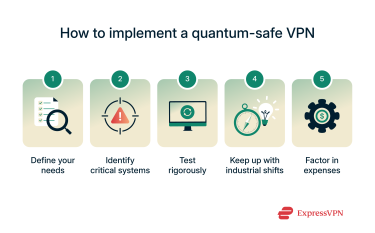
- Define your needs: Identify what goals you want to achieve with a quantum-safe VPN. The common goal is to secure your data and communications, but get granular for more insights that could help dictate the right choice. For instance, ML-KEM-powered quantum VPNs may be best for securing communications over websites, while Fast Fourier Lattice-based Compact Signatures over NTRU (Falcon)-powered VPNs perform better with remote identity verification.
- Identify critical systems: Audit your data and systems to identify areas where PQC must be applied right now and which systems can be migrated later. Critical systems will include those holding patents, trade secrets, intellectual property, and other sensitive information.
- Test rigorously: Organizations should rigorously test PQC algorithms. These tests can be adapted to the business’s processes and data types, ensuring they qualify as a reliable protection strategy.
- Keep up with industrial shifts: The research on quantum computers has been ongoing for a long time, and the first fully working model is expected in the next 5-10 years. Stay in the loop so you can quickly adapt to address any vulnerabilities or shortcomings as the technology progresses.
- Factor in expenses: Developing a quantum-safe VPN in-house could be expensive, both in time and financial investment. Evaluate whether you’d rather hire in-house experts or work with third-party providers.
Avoiding common pitfalls in PQC integration
Ensure your PQC integration goes smoothly by taking these potential issues into account:
- New performance costs: The complex nature of PQC means you’ll need more computing power. That may introduce additional business costs, such as upgrading or improving server infrastructure.
- Compatibility issues: Most computers aren’t equipped with PQC compatibility yet, so it’s best to ensure your deployment remains backward-compatible with current devices.
- Speed and performance issues: VPNs already impact internet connection speed due to the encryption process. Now, with PQC introducing a higher level of encryption, users may notice speed and performance differences compared to before. That’s why ExpressVPN built Lightway, an ultra-fast, quantum-safe VPN protocol with negligible speed impact.
- Security perception: No PQC should be trusted as 100% safe yet. They’ve not been extensively tested like the AES and RSA protocols, mainly due to the fact that their future attackers (quantum computers) aren’t fully online yet. Therefore, it’s important to remain alert to any changes in the PQC world and adapt accordingly.
When to start transitioning to a quantum-safe VPN
The best time to transition to a quantum-safe VPN was yesterday. The next best time is now. Of course, quantum computers haven’t gone mainstream yet, and we still have a few years before they do. However, cybercriminals and other entities are already harvesting data and storing it for decryption when quantum computers come fully online.
Once you move to a quantum-safe VPN, your sensitive data can only be intercepted and stored in a format that even quantum computers won’t be able to crack in a feasible amount of time.
FAQ: Common questions about quantum VPNs
What is a quantum VPN?
A quantum VPN is a type of VPN designed to protect users from having their secure encryption broken by quantum computers. Quantum VPNs use post-quantum cryptographic encryption models to introduce much more complex mathematical problems, which quantum computers should be unable to solve in a reasonable time.
Which is the most powerful VPN in the world?
The most powerful VPN against quantum computers depends on your specific encryption needs, the post-quantum cryptography (PQC) it uses, and its key encapsulation mechanism (KEM) strategy. Considering these factors will help you choose a VPN that encrypts your data in a way that ensures improved online privacy and security against the computational power of quantum computers.
What is the dark side of quantum computing?
Quantum computing has many positive potential uses. For example, it can allow scientists and researchers to run simulations faster and more efficiently, leading to more breakthroughs.
However, the power of quantum computers can also be targeted at breaking encryption protocols like Advanced Encryption Standard (AES), Rivest–Shamir–Adleman (RSA), and elliptic curve cryptography (ECC), leaking sensitive data to threat actors. That kind of information can be sold on the dark web, leaked to competitors (in the case of company secrets), or even become a national security issue (in the case of national secrets).
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN