What is browser fingerprinting? 7 ways to stop it (2025 guide)

Just as we leave physical fingerprints on the surfaces we touch, we also leave digital fingerprints on the websites we visit.
This online fingerprinting can quietly track you across the web, without the need for cookies or account logins. It's a sneaky way advertisers, trackers, and even some websites can recognize you based on your device, browser settings, and habits.
But the good news? There are ways to make your digital fingerprint much harder to pin down. Let’s break down what browser fingerprinting is and how you can stop it.
What are browser fingerprints?
Browser fingerprints are like digital ID cards created from the unique details of your device and browser. When you visit a website, it can gather information such as your OS, browser version, screen resolution, language settings, time zone, installed extensions, and even your keyboard layout. On their own, these details might not seem revealing, but when combined, they create a fingerprint that’s often unique to you.
Websites and trackers can use this fingerprint to recognize and follow you across different sites, even if you’re not logged in or using private browsing. While some businesses use fingerprinting for security and fraud prevention, it also raises big questions about privacy, especially since it happens silently in the background without needing your permission.
Browser fingerprinting vs. cookies
Both browser fingerprinting and cookies are used to track users online and gather information for things like personalization or advertising. But they work in very different ways.
Cookies store small bits of data on your device (like your login status or site preferences), which websites can read when you return, helping them remember you or customize content.
Fingerprinting, on the other hand, doesn’t store anything on your device. Instead, it collects details about your browser and device, like your OS, installed fonts, or screen resolution, to create a unique “digital fingerprint” that can be used to recognize you across visits.
One key difference is awareness: data privacy regulations, like the EU e‑Privacy Directive, require websites to notify users about cookies and request consent, so most people know they’re being used. Fingerprinting, however, often happens quietly in the background, making it harder to detect or control.
Browser fingerprinting vs. IP tracking
IP tracking focuses on your public IP address, the one assigned to your device by your internet service provider when you connect to the internet. This address helps identify your connection and can even reveal your rough geographic location.
Browser fingerprinting, on the other hand, gathers a wide range of details about your browser and device (like your OS, screen resolution, and installed fonts) to create a unique digital fingerprint.
The key difference? IP tracking is easier to block because you can hide your public IP using a VPN or proxy, while browser fingerprinting is much harder to avoid since it relies on dozens of subtle data points that aren’t as easy to mask.
Browser fingerprinting vs. device fingerprinting
You might hear “browser fingerprinting” and “device fingerprinting” used interchangeably, but they’re not quite the same.
Browser fingerprinting focuses specifically on identifying users based on data collected through the browser, like the browser version, language settings, time zone, and installed plugins or extensions. It works within the browser environment to build a unique profile of the user’s setup.
Device fingerprinting, on the other hand, goes a step further. It aims to recognize the entire device, no matter which browser or app is being used. This method is especially common in mobile environments, where it can pull signals from the OS, hardware, and other sensors: things that vary between iOS, Android, and other platforms. Device fingerprinting can still recognize a user even if the app’s cache is cleared or the browser is changed.
Learn more: Check out more ways of how third parties can be snooping on your online activities.
How does browser fingerprinting work?
When you load a website, small bits of code (usually JavaScript) run in the background to quietly collect technical details from your browser. Some of this data is shared automatically, like your browser type or OS. But fingerprinting scripts can go further, actively probing for more signals, such as which plugins you have installed, how your browser handles graphics (via WebGL), or even how your audio system responds.
Once all these pieces are gathered, they’re combined into a single, unique identifier, usually in the form of a hash. This fingerprint doesn’t store your name or email, but it can still be used to recognize you across different visits, even if you’ve cleared your cookies or switched to private mode. 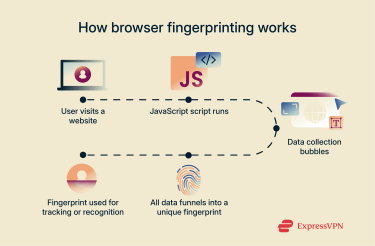 Because the fingerprint remains consistent as long as your setup stays the same, websites can use it to track returning visitors or flag suspicious behavior, often without needing your consent.
Because the fingerprint remains consistent as long as your setup stays the same, websites can use it to track returning visitors or flag suspicious behavior, often without needing your consent.
What kind of data is collected?
Browser fingerprinting gathers a wide range of signals from your browser and system setup, such as:
- Browser type and version.
- OS.
- Screen resolution and color depth.
- Time zone and language preferences.
- Installed fonts, extensions, and plugins.
- WebGL and audio processing capabilities.
- Battery status and available device memory.
- IP address (when not masked).
- Current browser window dimensions.
- Whether cookies are enabled.
- CPU type.
How accurate is fingerprinting in identifying users?
Browser fingerprinting can be highly precise. Some technologies report over 90% accuracy in identifying users, even without cookies or logins. For developers and site owners, that means they can reliably recognize returning visitors. For everyone else, it’s another reason to take privacy protection seriously.
Is browser fingerprinting legal?
Yes, if it follows privacy laws. Regulations like the General Data Protection Regulation (GDPR) (Article 4 and Recital 30) in the EU and the California Consumer Privacy Act (CCPA) (§1798.140(o)) in the U.S. treat browser fingerprints as personal data because they can uniquely identify you. That means companies must have a lawful reason, such as your consent under GDPR or providing notice and opt‑out options under CCPA, before collecting or using them.
How browser fingerprinting can be misused
Website owners can use browser fingerprinting to track users without their consent, often shaping their online experience in ways that aren't always visible or fair. These fingerprints can fuel hyper-targeted, intrusive ad campaigns or be used for profiling, potentially leading to discrimination based on things like device type or browsing behavior. In some cases, companies may even sell this data to third parties without users’ permission.
Worse still, if that data is ever leaked or mishandled, it could fall into the hands of malicious actors who might use it to impersonate users or commit fraud. In fact, browser fingerprints can even be manipulated to frame people for crimes they didn’t commit.
How common is browser fingerprinting?
Browser fingerprinting is more widespread than you might think. In recent years, it’s become a popular tool for tracking users online, often without their knowledge. A 2020 study found that around 25% of the top 10,000 websites were using fingerprinting techniques.
While some sites use it for helpful purposes, like preventing fraud or customizing user experiences, others use it in more intrusive ways, such as tracking users across sites or serving hyper-targeted ads without consent.
Who uses browser fingerprinting?
Browser fingerprinting is used by a wide range of industries, but it’s most common in:
- Online advertising and analytics: Tracking users across sites, measuring ad performance, and building detailed user profiles.
- E‑commerce: Personalizing recommendations and detecting payment fraud.
- Financial services and banking: Spotting suspicious logins and preventing account takeovers.
- Healthcare: Protecting sensitive patient data and verifying access.
- Government and public services: Securing portals and detecting fraudulent activity.
Different browser fingerprinting techniques
Browser fingerprinting is one of the more advanced methods of browser tracking, using various tools and scripts to collect detailed information about your setup. Here are some of the most common techniques:
- Canvas fingerprinting: Many websites use HTML5, which includes a feature called the canvas element. Fingerprinting scripts can instruct your browser to draw a hidden image on the canvas. The way your device renders that image (based on your graphics card, OS, and installed fonts) helps create a unique fingerprint.
- WebGL fingerprinting: Web Graphics Library is a JavaScript API used to render interactive graphics in your browser. WebGL fingerprinting works similarly to canvas fingerprinting but can gather even more detailed information about your graphics card and drivers.
- Audio fingerprinting: This method plays a brief, inaudible sound file and measures how your device processes it. Differences in sound cards, audio drivers, and OSs can all influence the results, making it another tool for browser tracking.
- Font fingerprinting: Also known as font detection, this technique checks which fonts are installed on your device. Because font libraries often vary by user, OS, or personal customization, it’s a highly effective way to help distinguish users.
- Media device fingerprinting: Some scripts try to detect what media devices (like webcams, microphones, or even internal video cards) are connected to your device. While browsers often require permissions for full access, partial information can still be gathered behind the scenes.
- Transport Layer Security (TLS) fingerprinting: This method uses information from the TLS handshake, a process that happens when your browser connects securely to a site, to collect data about your device and software. Even though TLS is meant to enhance privacy, it can also be repurposed for fingerprinting.
How browser fingerprinting is used in fraud detection
While browser fingerprinting often raises privacy concerns, it also plays an important role in security, particularly in detecting and preventing online fraud. Its ability to identify users without relying on cookies or IP addresses makes it a powerful tool in spotting suspicious behavior and stopping threats early.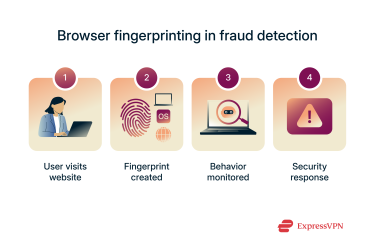
Identifying suspicious user behavior
By combining multiple fingerprinting techniques, websites can create highly accurate digital IDs for their visitors. These unique identifiers can then be used to detect anomalies, like when someone who usually logs in from the same setup suddenly accesses the site using a new device or configuration. That could signal a stolen login attempt or an account takeover in progress.
Preventing account takeovers and bot attacks
Account takeovers, where hackers use stolen credentials to break into user accounts, are among the most common types of online fraud. Fingerprinting helps flag unusual login activity without adding friction for trusted users, allowing security systems to apply extra verification only when needed.
It’s also effective against bot attacks and brute-force strategies. Bots often rely on generic or repetitive browser setups. By recognizing these patterns early, fingerprinting allows websites to stop bad actors before they do damage, even if they haven’t yet triggered traditional security thresholds.
Bypassing traditional concealment techniques
Fraudsters often try to hide their identity using virtual machines (VMs) or by blocking cookies. But unlike IP addresses or cookies, browser fingerprints are much harder to disguise or reset. This makes them a valuable tool for identifying users who attempt to mask their activity. Even the National Security Agency (NSA) has been known to use advertising cookies and browser identifiers to track users online.
How do you check if your browser is being monitored?
Your browser is probably being monitored in some way whenever you browse the web. While fingerprinting is designed to be invisible, there are ways to detect it or learn more about what makes your setup unique.
You might not notice the tracking directly, but its effects can show up in subtle ways, such as:
- Ads that closely reflect your interests, behavior, or location.
- Product recommendations that feel strangely personal.
- Online prices that seem to change depending on your device or browser.
Browser fingerprinting test tools
If you want a clearer picture of how your browser is being monitored, try these free tools:
- FPMON: A real-time fingerprinting monitor for Google Chrome. It runs in the background and alerts you whenever a site attempts to fingerprint your browser, helping you pinpoint which pages are tracking you.
- AmIUnique: This research-based tool shows you what fingerprintable information your browser reveals. It also gives you a "uniqueness score" to help you understand how easily you could be identified online.
- BrowserLeaks: A comprehensive set of tests that analyze your browser’s privacy exposure. You can check for canvas and font fingerprinting, WebGL data leaks, and more, all in one place.
How to stop or reduce browser fingerprinting
You can’t completely block browser fingerprinting, since some of it happens as part of how websites interact with your browser. But you can limit how much data is collected and make it harder for trackers to create a reliable fingerprint of your device.
Use a privacy-focused browser
Some browsers are better at protecting your fingerprint than others. If you're serious about privacy, consider switching to one designed to resist tracking:
- Tor is one of the best options for anti-fingerprinting. It uses a technique called letterboxing, along with other anti-fingerprinting measures, to make it harder for companies that use fingerprinting to obtain identifying information about their users.
- Brave offers built-in protections against trackers and fingerprinting that are designed to make fingerprinting a less effective form of tracking.
- Firefox is also strong in this area. Its Enhanced Tracking Protection automatically blocks known fingerprinters and limits how much information your browser sends to suspected fingerprinters.
You can also use private mode, like Chrome’s Incognito or Firefox’s Private Browsing. While they don’t stop fingerprinting, they can reduce certain identifiable data points, such as your list of active extensions, making your fingerprint slightly less unique.
Bonus tip: Use different browsers for different tasks (for example, one for work and one for personal use). This segmentation makes it much harder for trackers to build a unified digital profile of you.
Disable JavaScript
JavaScript and the now-obsolete Adobe Flash have historically been major sources of fingerprinting data. A 2019 dissertation found that JavaScript could expose over 47,000 unique plugin configurations, while Flash revealed more than 36,000 font variations, making both valuable tools for trackers in the past.
Today, Flash is largely irrelevant. It’s no longer supported by Adobe or any modern browser, so disabling it has no negative impact, and it’s likely already disabled by default.
JavaScript, however, is still widely used. Disabling it can significantly reduce fingerprinting, blocking scripts from accessing data like your fonts, plugins, and even tracking cookies. But there’s a trade-off: many websites rely on JavaScript to function, so turning it off entirely may break parts of those sites.
A more flexible solution is using a browser extension like NoScript, which allows you to control where and when JavaScript runs. This not only limits fingerprinting but can also help protect against cross-site tracking, a common tactic used by advertisers and data brokers.
Install anti-fingerprinting browser extensions
Most major browsers support extensions that can enhance your online privacy and help reduce fingerprinting. These tools often block trackers, delete cookies, mask fingerprint signals, or prevent scripts from running in the first place.
Some popular (and free) options include:
- uBlock Origin Lite: Lightweight content blocker that blocks trackers and ads.
- Privacy Badger: Developed by the Electronic Frontier Foundation (EFF), it automatically blocks invisible trackers.
- Fingerprint Defender: Randomizes fingerprint values to confuse trackers.
- Canvas Blocker: Specifically targets canvas fingerprinting techniques.
- FPMON: As mentioned earlier, it alerts you in real time when a site tries to fingerprint your browser.
- Cookie AutoDelete: Automatically removes cookies from sites you no longer visit.
While these tools are effective, keep in mind that using too many extensions at once can slow down your browser or create conflicts. Choose a few trusted ones that match your needs and keep them updated.
Use a VPN
A VPN can’t stop browser fingerprinting entirely, but it still does a lot to protect your privacy.
Fingerprinting collects details from your browser, but a top-notch VPN like ExpressVPN hides your IP address and encrypts your traffic, making it much harder to link your online activity to your real identity.
Even if a site gathers some fingerprint data, your masked IP and encrypted connection help keep your browsing private, especially when your VPN server is shared with many other users.
So while a VPN doesn’t block fingerprinting, it takes IP tracking out of the picture, making it much harder to connect any fingerprint data to your real identity or location.
Learn more: If you’re concerned about internet service provider (ISP) tracking, check out the best ways to keep your browsing history hidden from your ISP.
Use virtual machines (VMs) to isolate browser fingerprints
If you’re technically inclined, consider using a VM to create a separate internet browsing environment. Fingerprints gathered inside the VM will reflect the virtual system rather than your actual hardware.
However, this doesn’t make you immune to fingerprinting, as your VM will still generate a unique fingerprint based on its own configuration. If you always browse from the same VM, trackers can still recognize and follow you. The main advantage is separating your real device’s details from what’s exposed online, which can be useful for compartmentalizing sensitive tasks.
Keep in mind that setting up and managing a VM can be complex, so this method is best suited for advanced users.
FAQ: Common questions about browser fingerprinting
What is fingerprinting in cybersecurity?
In cybersecurity, fingerprinting refers to the process of collecting information about a device, browser, or system to uniquely identify it. It’s often used for tracking, profiling, or detecting suspicious activity.
Is browser fingerprinting more invasive than cookies?
Yes, fingerprinting is regarded as more invasive than cookies, since users are often unaware that fingerprinting is even occurring and can’t stop it in the same way that they can opt out of cookie collection or delete cookies manually via their browser settings.
Can I completely avoid being fingerprinted?
No, it’s effectively impossible to completely avoid browser/device fingerprinting. However, you can take steps to minimize the amount of data that website owners and trackers are able to gather about you. Helpful ways to reduce browser fingerprinting include installing a VPN, switching to a privacy-focused browser, and installing anti-fingerprinting extensions.
Does private browsing prevent fingerprinting?
No, private browsing (like the Incognito mode) doesn’t prevent fingerprinting. All it does is prevent your browser from storing cookies and cached data from the sites you visit, as well as recording those sites in your browsing history. It doesn’t stop websites from seeing your digital fingerprint details, like which browser you’re using, what time zone you’re in, etc.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN















Comments
This blog provides useful information about new techniques and concepts.very impressive lines are given which is very attractive.
I can't see
Old post but informative even for now.